Byzantine Fault Tolerance (BFT) is a consensus mechanism that works on resolving Byzantine Generals’ problem in a decentralized network.
Introduction
With regards to agreement conversation, the Byzantine general's concern is one of the most complicated and dubious. In 2008, with the origin of Bitcoin, Satoshi Nakamoto professed to tackle the byzantine issue with the proof of work (PoW) agreement system. Notwithstanding, it was only the most vital phase in accomplishing agreement in a decentralized network. This article will make sense of the Byzantine concern and Byzantine Fault Tolerance (BFT) Agreement Component in Blockchain. It further goes through a practical byzantine fault tolerance (pBFT) agreement way to deal with tackle the issue.
Let’s start with
the Byzantine general’s concern.
What is the Byzantine Generals' Concern?
Byzantine Generals'
concern was recognized in 1982 as a consistent choice riddle. Its premise on
how generals of similar side with various troops could have a communication concern
in making decisions about the next move against the enemy.
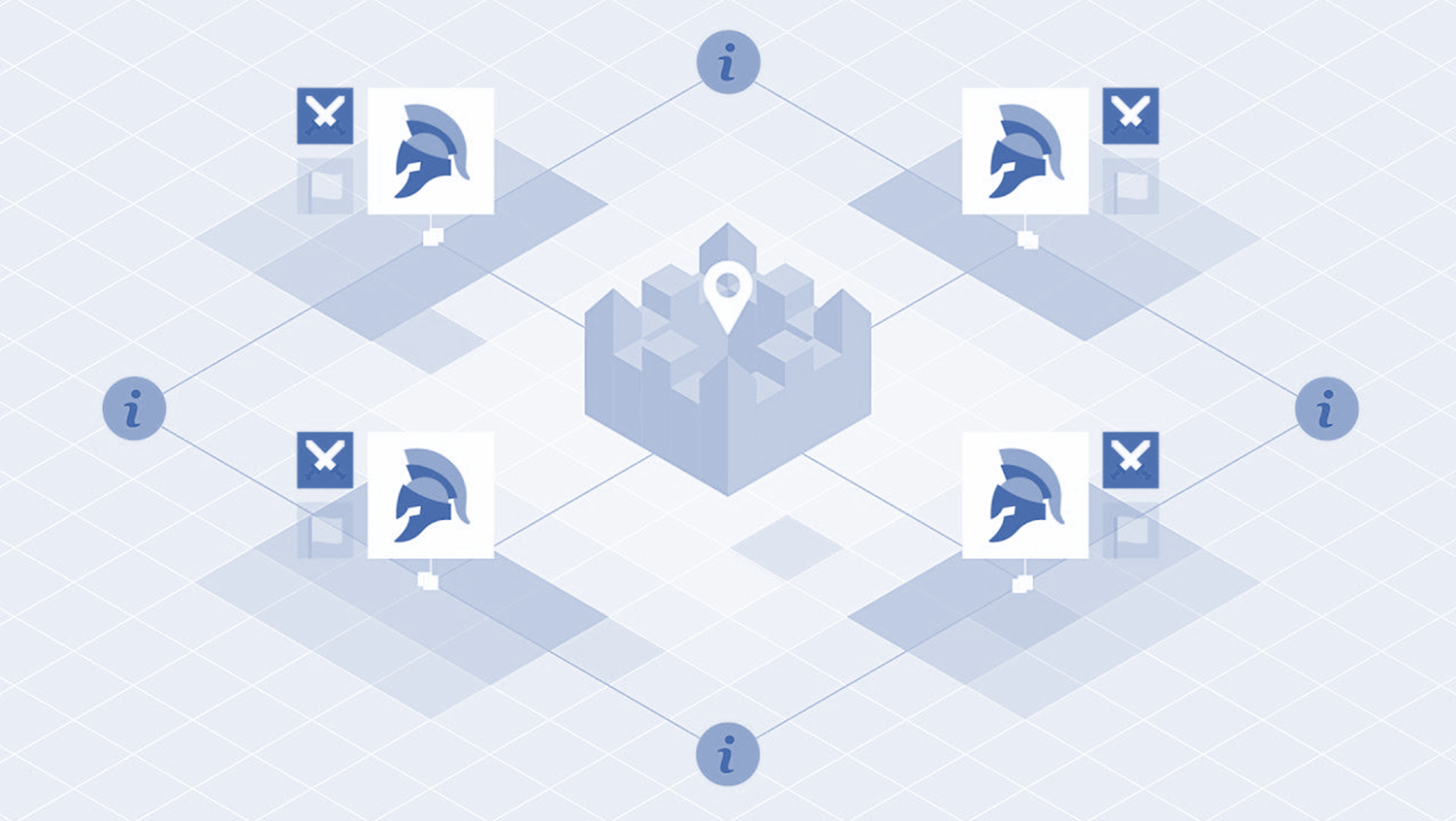
Let’s see the
below diagram to completely figure out the issue.
The issue states
like a gathering of generals with their army are going to go after their enemy.
They encompassed the enemy's palace from 4 distinct bearings. Presently how
might they convey the choice of going after or withdrawing simultaneously?
Here, a synchronized
and simultaneous assault on the enemy will be a success.
Following are issues that might emerge while
sharing the choice starting with one general then onto the next:
- ·
The
messenger could get captured while conveying the decision.
- ·
Imagine
a scenario in which a sham modified the message got.
- ·
How
might a general ensure in the event that he got the message from the normal
general?
- ·
Imagine
a scenario in which other general become backstabbers and they send the message
to assault, yet they really retreat.
How might the
framework be certain that each broad will go after simultaneously from their
assigned area? Is it basically impossible yet to trust each other totally?
Blockchain
appears to determine this issue with the Byzantine fault tolerance (BFT)
agreement component.
What is Byzantine Fault Tolerance (BFT)?
To guarantee the outcome of the generals'
group, they need a calculation that could stick to the accompanying
circumstances:
- ·
All
the troop generals need to settle on the following activity of the arrangement.
- ·
The
generals ought to be dependable and faithful to the framework.
- ·
Generals
should not get impacted to become network double crossers.
- ·
They
need to follow the calculation of the framework.
- ·
The
gathering of generals needs to arrive at an agreement or choice, regardless of
the swindlers' activities.
- ·
The
framework or network shouldn't prompt a 51% assault anytime of activity.
Byzantine Fault
Tolerance (BFT) is an agreement approach
that opposes a framework to get into the Byzantine Generals' concern. It
additionally implies the framework ought to remain in one piece regardless of
whether one of the nodes (or general) falls flat. Also, BFT expects to lessen
the impact of malevolent byzantine nodes (or general) on the network.
What is Practical Byzantine Fault Tolerance
(PBFT)?
While trying to
conquer the Byzantine issues, Barbara Liskov and Miguel Castro presented a
Practical Byzantine Fault Tolerance (pBFT) agreement calculation in 1999. They
mean to guarantee a reasonable byzantine state machine replication for enduring
vindictive or byzantine nodes.
The pBFT follows a nonconcurring approach.
Coming up next are fundamental parts of the pBFT agreement calculation:
- ·
All
nodes are gathered in a succession.
- ·
One
network node fills in as a pioneer node, and most of them are reinforcement
nodes.
- ·
The
essential or pioneer node serves the client's solicitation. It fills in as a
mediator among client and reinforcement nodes.
- ·
All
nodes are equipped for speaking with different nodes to really take a look at
the fair nodes.
- ·
Fair
nodes ought to have the option to arrive at an agreement for the following
worldwide change in the network in light of larger part rule.
- ·
It
distinguishes the wellspring of the message to ensure it's sent by the right
shipper.
- ·
Guarantees
the message has not been adjusted or in the middle between.
As we went
through the standards of pBFT. How about we perceive how it functions?
How does the PBFT Algorithm work?
The PBT exceptionally
relies upon the condition that the most extreme number of noxious or byzantine nodes
should surpass 33% of the multitude of nodes in the network. Subsequently, the
security of the network is straightforwardly reliant upon the quantity of
absolute legit nodes.
So, a pBFT
framework can deal with 'f' broken or byzantine nodes where there are 3f + 1
complete number of nodes on the network.
Following is the course of pBFT agreement
calculation:
- ·
A
user sends a solicitation to the pioneer node.
- ·
Then
the pioneer node floods the solicitation to all reinforcement nodes.
- ·
Every
one of the nodes work on the solicitation and send an answer to the user.
- ·
The
user sits tight for (f + 1) answers from every one of the nodes with a similar
outcome. Here, f = number of conceivable broken nodes.
·
The pBFT instrument comprises of 3 phases:
- ·
Pre-prepare phase: The pioneer node conveys a pre-arranged
message to every reinforcement node.
- ·
Prepare: Subsequent to getting the pre-arranged
message from the pioneer, the reinforcement nodes send the pre-arranged message
as an answer to any remaining nodes including the pioneer. A node is thought of
as arranged provided that it has gotten pre-arranged by the pioneer and seen
(2f + 1) number of arranged messages from different nodes.
- ·
Commit: On the off chance that the nodes are ready,
they send a commit message. In the event that a node gets (f + 1) commit
messages, they complete the client's solicitation.
The beneath chart
shows the working of the pBFT calculation.
The entire course
of check in a circulated framework utilizes the idea of computerized marks. The
legitimacy message and source are guaranteed utilizing arrangement numbers and
metadata.
Blockchain like
Zilliqa, Hyperledger texture, and Tendermint purposes the Useful Practical
Byzantine Fault Tolerance (pBFT) calculation.
Advantages of PBFT
Following are the benefits of the pBFT
agreement calculation:
·
A
pBFT doesn't need completing high numerical calculations like PoW.
·
It
is an energy-effective agreement model.
·
A
block of exchanges here doesn't have to follow numerous affirmations by every node.
Thus, it demands less investment.
·
As
pBFT requires each node to take an interest and serves the client demand, every
node gets the award. Thus low prize change between every node.
Limitation of PBFT
Following are the disadvantage of the pBFT
agreement calculation:
·
pBFT
has a high correspondence above that will increment with the quantity of nodes
in the network.
·
It
has adaptability issues with greater networks.
·
pBFT
is helpless to Sybil assaults in which one node controls or goes about as
different network nodes.
In Conclusion
In the above
article, we covered Byzantine Fault Tolerance (BFT) completely. Alongside its
functioning pros, and cons. Hope you learned and enjoyed reading this
article. Please share your comments and queries.
.png)
.png)

.png)
.png)
0 Comments